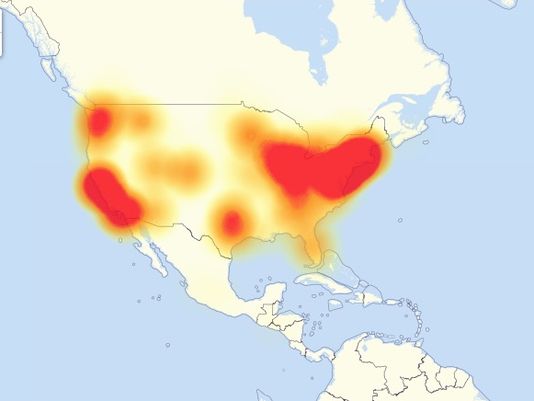
Students struggled to do their homework and connect to sites such as Facebook, Twitter and Spotify due to an Internet Distributed Denial of Service widespread attack, which originated in New Hampshire on Oct. 21. As election day approaches those in Silicon Valley fear the possibility of another attack, which would disturb voter turnout, according to CNN Money.
A widespread assault
Dyn, the company attacked, provides Domain Name Services to major companies around the world. The unknown attackers appeared to have used Internet-connected devices such as printers, Internet refrigerators and even Internet toasters to overload the infrastructure and block Internet access in heavily populated areas around the world, including Southern California.
“Someone essentially was able to take over, take advantage of a lot of… connected devices,” said Scott Himes, Biola director of network operations. “What’s funny about these kinds of attacks is that… all of these devices are doing things that are just perfectly normal, it’s just that you’ve got millions of them doing it all at the same time, so it’s really taking advantage of scale.”
Increasing vulnerability
The scale of the event largely has to do with how the Internet has changed over time, so even though DDoS attacks have been around, the shift in the Internet makes them a big issue.
“The way the Internet has grown up, it’s very vulnerable to this kind of attack, so it takes infrastructure changes. So it’s like moving load bearing walls to fix this problem,” said Steve Earle, senior director of Information Technology.
Biola’s main DNS provider, Google, did not work properly because of the DDoS attack, along with many other upstream providers. However, the Biola Guest network connects to a different provider, OpenDNS, which did not fail. By using Biola Guest, IT troubleshooted and later identified the problem.
“DNS is a critical Internet infrastructure piece. If DNS isn’t working, then you can’t get to sites, and that’s what we saw essentially, because DNS is what’s making the translation between your computer and the website you’re trying to get to,” Himes said.
Since the higher-level providers were not in operation, however, IT lacked the capability to handle the situation. In response, IT continually cleared the cache to keep the DNS on campus fresh, according to Himes.
The cyberattack contradicted what people expected in that many websites, including Netflix and Amazon, were shut down not to steal people’s passwords but to block access.
“Really, it’s an attack on availability, not an attack against information. So it’s not that these attackers are trying to steal data or get personal information, any of that kind of stuff, really. Their whole goal is deny you access, shut down availability,” Himes said.
A lack of access
One of the ways students had a lack of access included trying to complete their homework. However, several other students were not aware of what happened because of traveling or camping, and not trying to complete homework.
“I was trying to do homework and I was trying to Google some things, but I wasn’t able to because it just wouldn’t show me any search results whatsoever so it was a bit of a hassle that day,” said Bethel Raposas, junior humanities major.
On the day of the attack, IT searched for an upstream DNS provider, which gives service to another server, such as Google, that would work the best. The Biola Guest network through OpenDNS remained working.
The issue remains larger than Biola and the solutions here do not necessarily reflect those across the U.S. IT has begun looking into moving providers to Amazon to reduce the effects of future potential cyberattacks.
“We’re in the process of moving some of our services to Amazon to leverage Amazon’s cloud services because they are a major global player and accessible to the world with a much wider global infrastructure than here on our one site,” Himes said.