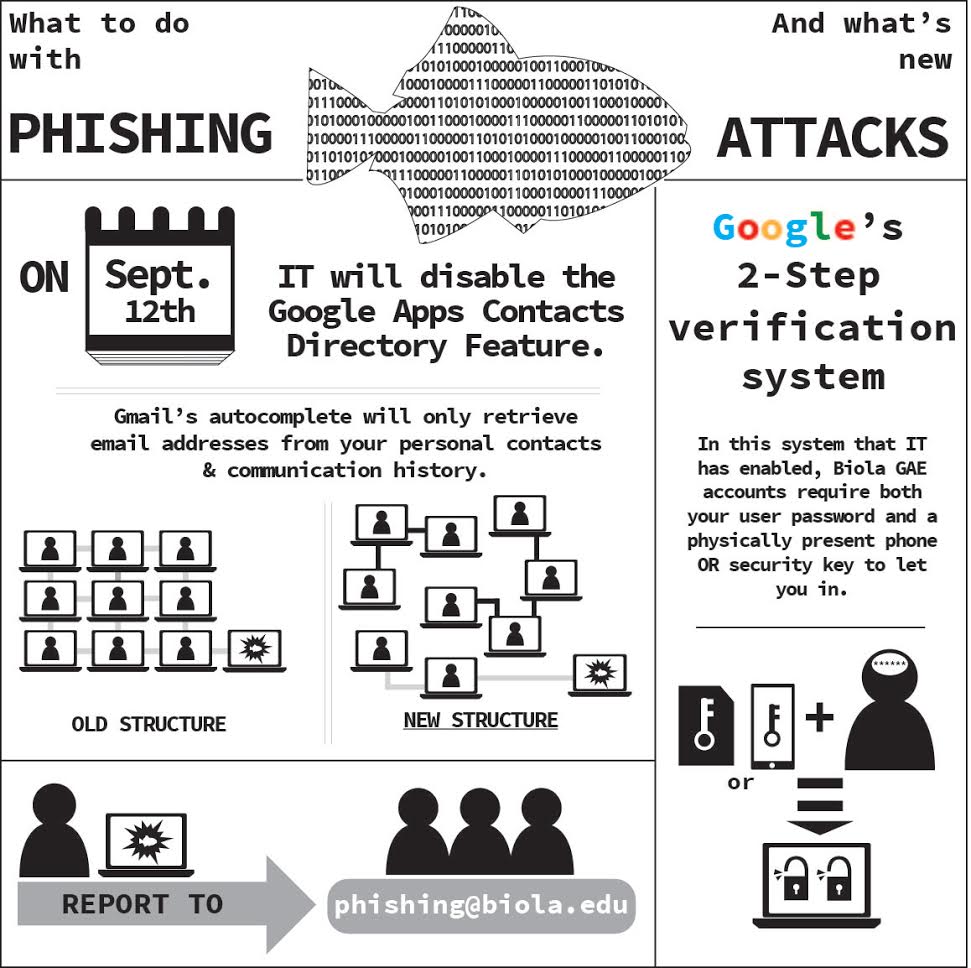
Information Technology will be requiring two-step verification for Biola email accounts after a large wave of phishing email attacks started in late May of this year. While Biola email account users encountered a small numbers of attacks in recent years, a larger number of attacks have occured over the summer months into beginning of this fall semester.
Compromised Accounts
“We’ve received [phishing emails] off and on for several years, but the large increase happened in late May and early June is when they started to become really noticeable where it seemed we started to become a target for them,” said Ben Wright, director of IT.
A total of 375 email accounts have been compromised since late May — 208 student accounts, 143 alumni accounts and 24 employee accounts.
Email accounts become compromised when users enter their usernames and passwords in the Google Forms document included in each spam email. Lisa Holm, junior human biology major, noticed emails in the beginning in August. Though she did click on the link, she never entered her information.
“I didn’t submit my information but I did click on the link at the bottom. I didn’t [submit information] because I thought it was weird that they asked for my password again,” Holm said.
International Origins
Though the phishing emails are sent out by automated programs, the individuals behind the emails originate from countries outside the U.S.
“As far as the location of the people behind the emails, it’s almost entirely abroad. Probably the largest number come from accounts that are compromised from Nigeria, we see some from like Cambodia, Vietnam, China ― that’s where you can see people have logged into,” Wright said.
It is difficult to determine whether an account is compromised until the emails are sent out through the account. When this happens, Google is likely to alert IT when suspicious activity is detected.
“It’s typically after an account’s been used to send other emails and they recognize that a high volume of emails of this type of content are being sent from this account,” Wright said.
Securing the Account
Once an account has been verified as compromised, Google will secure the account and IT will clear all user access before returning it to the original owner.
However, not all students have been affected by the phishing emails. Naomi Martiniuc, freshman pre-clinical nursing major, is relieved she was not affected by the malicious emails.
“I actually haven’t gotten any of those,” Martiniuc said. “I’m happy I don’t get them and I’m happy that I wasn’t one of the first people to get it because I probably would have gone through with whatever it was asking because it seems important.”
The IT department urges students and alumni to enable two-step verification that requires users to input their password and a code that can be sent through text, phone call, mobile app or even a security key that can be inserted into a computer’s USB port.